What do you do when it’s been 15 months since your entire team has been in the office, and you also want to improve your web application security skills? A hackathon!

With Covid restrictions lifting and the vaccination rate increasing, the Elements engineering team organized an in person, in office hackathon focused on security vulnerabilities, with a little help from the local pizzeria 😉
Preparing the hackathon
Security is a big priority for our teams, and Elements’ participation in Atlassian Bug Bounty means engineers are regularly working to improve our apps’ security. But why wait for bugs to be found when you can develop your skills as a team? Software developer Houssem Aloulou had previously participated in and helped organize Hackfests during his studies in Tunisia, and had lots of ideas about how Elements could hold its own hackathon. Focused on web application security, Houssem prepared the event using the Catch the flag (CTF) format.

“I chose the Catch the Flag format because it’s culture is really rich, with a focus on the experience, where collaborating and sharing knowledge between team members is the main focus.”
Ready, set, code!
On Monday June 21, 19 Elements engineers were randomly split into 5 different teams to work on the 9 challenges. Equipped with fun t-shirts and snacks, engineers worked from 10 am to 4pm.
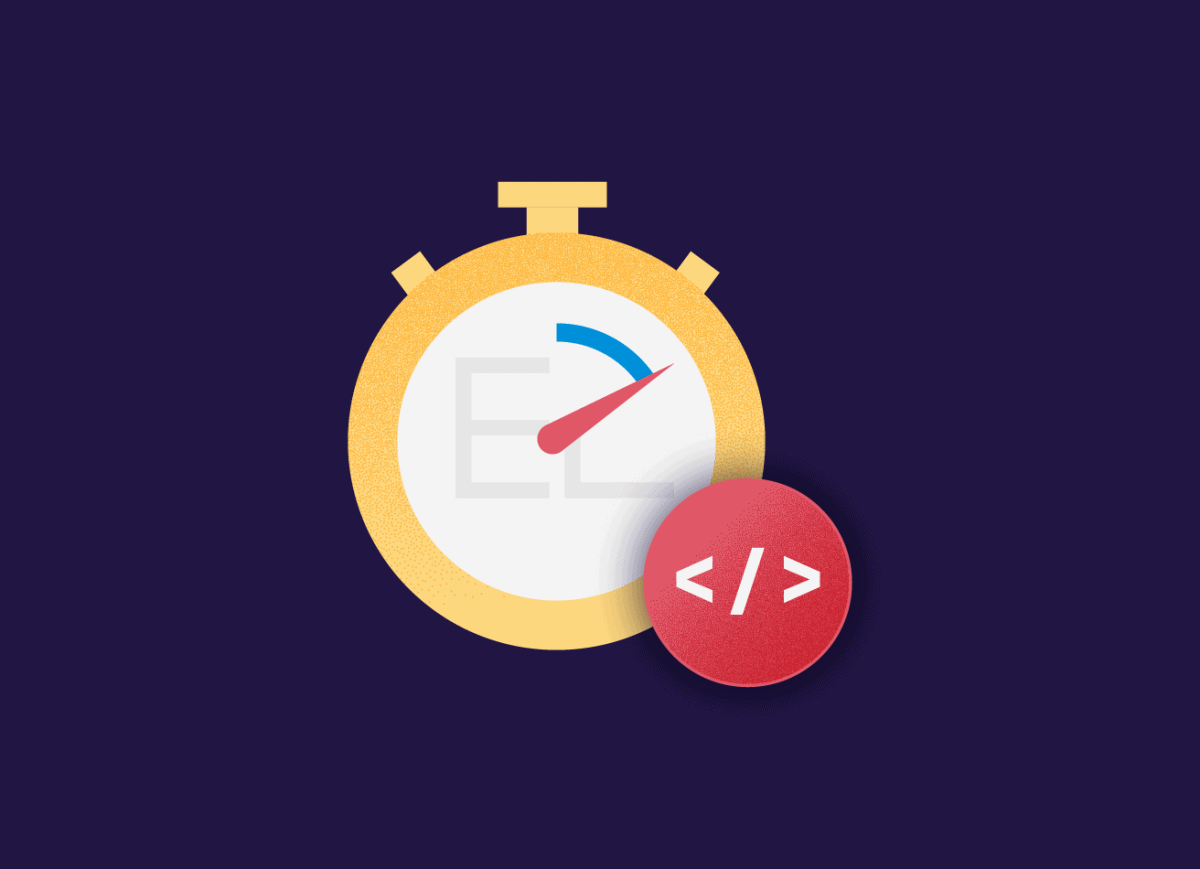
Each challenge earned teams a number of points based on the difficulty, and with half an hour to go before the end of the day, team <script>alert(*La Bamboche*)</script> finished all 9 challenges, with team ILOVEYOU in a strong second place just 2 minutes later.

Houssem explains how he set up the challenges: “I took examples from real security problems we have faced, and wanted participants to think about the impact of those kinds of bugs. The challenges used several servers with several vulnerabilities, and the team that exploited the vulnerability found the flag.”
Each challenge earned teams different points, based on the difficulty, but using hints reduced the earn-able points. Some people tried to get Houssem to reveal a few secrets, but his lips were sealed! An hour before the end of the event, the team scores were hidden so teams didn’t know how close the competition was.
Looking back, and to the future
What did participants have to say about the event?
“A playful way to increase awareness around the different types of attacks and also to work as a team.”
“Inter-squad teams, working together, the escape game feeling: overall a great way to commit to memory the most important topics related to security.”
Based on the feedback, we hope to repeat the event in the future, potentially with more diverse challenges including server breach, man in the middle or other topics.
Sound like an event you’d like to participate in? We’re hiring!